Experts uncovered a new Osiris ransomware strain that used a custom POORTRY driver in a BYOVD attack to disable security tools & steal data in 2025.



An operational security failure allowed researchers to recover data that the INC ransomware gang stole from a dozen U.S. organizations.
A deep forensic examination of the artifacts left behind uncovered tooling that had not been used in the investigated attack, but exposed attacker infrastructure that stored data exfiltrated from multiple victims.
The operation was conducted by Cyber Centaurs, a digital forensics and incident response company that disclosed its success last November and now shared the full details with BleepingComputer.

Okta is warning about custom phishing kits built specifically for voice-based social engineering (vishing) attacks. BleepingComputer has learned that these kits are being used in active attacks to steal Okta SSO credentials for data theft.
In a new report released today by Okta, researchers explain that the phishing kits are sold as part of an “as a service” model and are actively being used by multiple hacking groups to target identity providers, including Google, Microsoft, and Okta, and cryptocurrency platforms.
Unlike typical static phishing pages, these adversary-in-the-middle platforms are designed for live interaction via voice calls, allowing attackers to change content and display dialogs in real time as a call progresses.

The developer of the popular curl command-line utility and library announced that the project will end its HackerOne security bug bounty program at the end of this month, after being overwhelmed by low-quality AI-generated vulnerability reports.
The change was first discovered in a pending commit to curl’s BUG-BOUNTY.md documentation, which removes all references to the HackerOne program.
Once merged, the file will be updated to state that the curl project no longer offers any rewards for reported bugs or vulnerabilities and will not help researchers obtain compensation from third parties either.
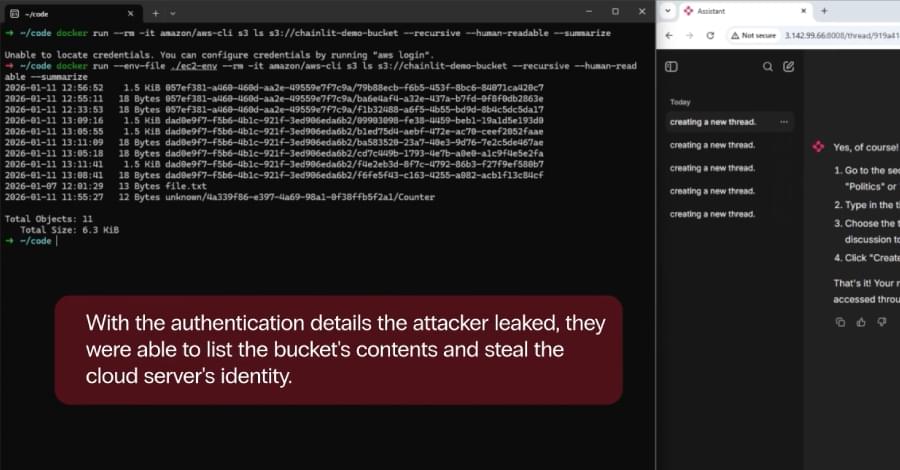
Security vulnerabilities were uncovered in the popular open-source artificial intelligence (AI) framework Chainlit that could allow attackers to steal sensitive data, which may allow for lateral movement within a susceptible organization.
Zafran Security said the high-severity flaws, collectively dubbed ChainLeak, could be abused to leak cloud environment API keys and steal sensitive files, or perform server-side request forgery (SSRF) attacks against servers hosting AI applications.
Chainlit is a framework for creating conversational chatbots. According to statistics shared by the Python Software Foundation, the package has been downloaded over 220,000 times over the past week. It has attracted a total of 7.3 million downloads to date.

People worldwide are being targeted by a massive spam wave originating from unsecured Zendesk support systems, with victims reporting receiving hundreds of emails with strange and sometimes alarming subject lines.
The wave of spam messages started on January 18th, with people reporting on social media that they received hundreds of emails.
While the messages do not appear to contain malicious links or obvious phishing attempts, the sheer volume and chaotic nature of the emails have made them highly confusing and potentially alarming for recipients.

A new family of Android click-fraud trojans leverages TensorFlow machine learning models to automatically detect and interact with specific advertisement elements.
The mechanism relies on visual analysis based on machine learning instead of predefined JavaScript click routines, and does not involve script-based DOM-level interaction like classic click-fraud trojans.
The threat actor is using TensorFlow.js, an open-source library developed by Google for training and deploying machine learning models in JavaScript. It permits running AI models in browsers or on servers using Node.js.


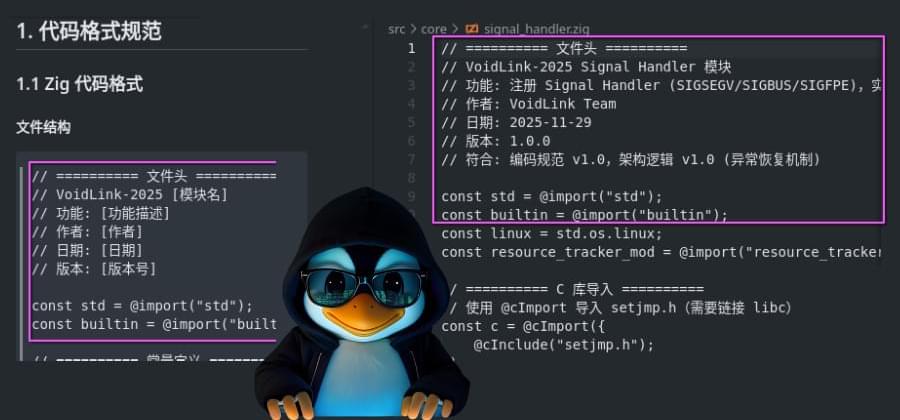
The recently discovered cloud-focused VoidLink malware framework is believed to have been developed by a single person with the help of an artificial intelligence model.
Check Point Research published details about VoidLink last week, describing it as an advanced Linux malware framework that offers custom loaders, implants, rootkit modules for evasion, and dozens of plugins that expand its functionality.
The researchers highlighted the malware framework’s sophistication, assessing that it was likely the product of Chinese developers “with strong proficiency across multiple programming languages.”