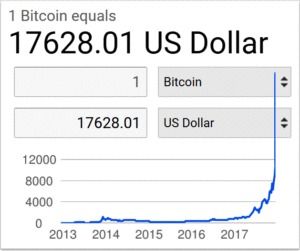
Bitcoin has many characteristics of a currency. It is portable, fungible, divisible, resistant to forgery, and it clearly has value. Today, that value came close to $20,000 per coin. Whether it has ‘intrinsic value’ is somewhat of a moot question, because the US dollar hasn’t exhibited this trait since 1972. Today, economists don’t even recognize the intrinsic value of gold—beyond a robust, international, supply-demand network.
Lately, Bitcoin is failing as a viable currency, at least for everyday consumer transactions. The settlement of each transaction is bogged down with long delays and a very high cost. The situation has become critical because of squabbling between miners, users and developers over how to offer speed transactions or lower the cost of settlement. Bitcoin forks and altcoins such as Dash and Bitcoin Cash demonstrate that these technical issues have solutions. Since Bitcoin is adaptable, I believe that these issues are temporary.
But an interesting question is not whether Bitcoin will eventually become a consumer currency. it is whether Bitcoin can distinguish itself as a store of value, rather than just an instrument for payment or debt settlement. After all, a Visa credit card, a traveler’s check and an Amazon gift card can all be used in retail payments, but none of them have value unless backed by someone or something. US Dollars on the other hand are perceived as inherently valuable. They carry the clout and gravitas of institutions and populations, without users questioning from where value arises. (This is changing, but bear with me)…
What about Bitcoin? Does owning some bitcoin represent a store of value? Yes: It absolutely does!
Bitcoin is a rapidly maturing two-sided network. Despite a meteoric rise in exchange value and wild fluctuations during the ride, it is the epitome of a stored value commodity. Regardless of government regulation, adoption as a consumer payment instrument, or the cost and speed of transactions, it has demonstrated stored value since May 22 2010, when Laszlo, a Bitcoin code developer, persuaded a restaurant to accept 10,000 BTC for 2 pizzas.
The “currency” accepted by the pizza parlor wasn’t a gift card. It was not backed by a government, a prior deposit, dollars, gold, the promise of redemption, or by threat of force or blackmail. When a large community of individuals value, exchange, and can easily authenticate something that has none of those underpinnings, that thing clearly has stored value.
In this case, value arises from its scarcity and a robust supply-demand-network. Because its value is not tied to a government or to other commodities, its exchange rate with other things will be bumpy, at first. But as it is recognized, traded and adopted as a stored value token, the wild spikes will smooth out.
A tipping point will precipitate rapid adoption when…
- when some vendors begin to quote prices in Bitcoin (rather than national currency)
- when some of these vendors retain a fraction of their bitcoin-revenue for future purchases, payments or debt settlements—rather than converting revenue to fiat/national currency with each sale
 Bitcoin is clearly a store of value, and it is beginning to displace gold and the US dollar as the recognized reserve currency (it is gradually becoming the new gold standard). But before Bitcoin can serve as a widely adopted everyday currency (i.e. as a payment instrument—with or without the stored value of a currency unto itself), it must first incorporate technical improvements that speed transactions and lower cost.
Bitcoin is clearly a store of value, and it is beginning to displace gold and the US dollar as the recognized reserve currency (it is gradually becoming the new gold standard). But before Bitcoin can serve as a widely adopted everyday currency (i.e. as a payment instrument—with or without the stored value of a currency unto itself), it must first incorporate technical improvements that speed transactions and lower cost.
This is taking longer than many enthusiasts would have liked. But, that’s OK with anyone who keeps their eye on the big picture. Democracy is sometimes very sloppy.
Philip Raymond co-chairs CRYPSA, publishes A Wild Duck and hosts the New York Bitcoin Event. Last month, he kicked off the Cryptocurrency Expo in Dubai. Click Here to inquire about a live presentation or consulting engagement.


 Bitcoin is clearly a store of value, and it is beginning to displace gold and the US dollar as the recognized reserve currency (it is gradually becoming the new gold standard). But before Bitcoin can serve as a widely adopted everyday currency (i.e. as a payment instrument—with or without the stored value of a currency unto itself), it must first incorporate technical improvements that speed transactions and lower cost.
Bitcoin is clearly a store of value, and it is beginning to displace gold and the US dollar as the recognized reserve currency (it is gradually becoming the new gold standard). But before Bitcoin can serve as a widely adopted everyday currency (i.e. as a payment instrument—with or without the stored value of a currency unto itself), it must first incorporate technical improvements that speed transactions and lower cost.